AWS and customers share security and compliance responsibilities when systems are built on the AWS cloud. AWS is responsible for the security of the cloud and customers are responsible for securing everything within their cloud.
Customers can take advantage of automated tools from AWS for securing their cloud and validating compliance. These services sprawl across several realms of security including data protection, identity and access management, infrastructure security, threat detection and continuous monitoring. The area of security and compliance in AWS is often poorly understood, and it can be difficult to understand the differences between services. This article aims to demystify these services and provide a simple explanation and comparison.
Security and Compliance Services Summary
* Please see the AWS pricing calculator for specific pricing details and the latest pricing information.
AWS Identity Access Management (IAM)
Category: Access Management
IAM controls access to AWS Cloud services and resources. All access, by default, is denied and only allowed when an IAM policy explicitly grants access. IAM is involved in every API request we make to AWS, handling more than 400 million API calls per second worldwide, according to this blog.
To get started using IAM, you can create an IAM role and grant it permissions. For your organisation’s workforce users, you can create a role that can be assumed by your identity provider. For workloads, you can create a role that can be assumed by the AWS service you are using, such as Amazon EC2 or AWS Lambda and attach the required permissions to the role. For more information, see Getting started with IAM.
AWS IAM Identity Center
Category: Access Management
This service is built on top of IAM to simplify access management across AWS accounts for organisations that adopted a multi-account strategy for their environment to centralise access control. You can either federate users from your preferred identity provider including; Azure AD, Okta, Ping Identity, JumpCloud, CyberArk, and OneLogin, as well as, Microsoft Active Directory Domain Services or directly create users in Identity Center.
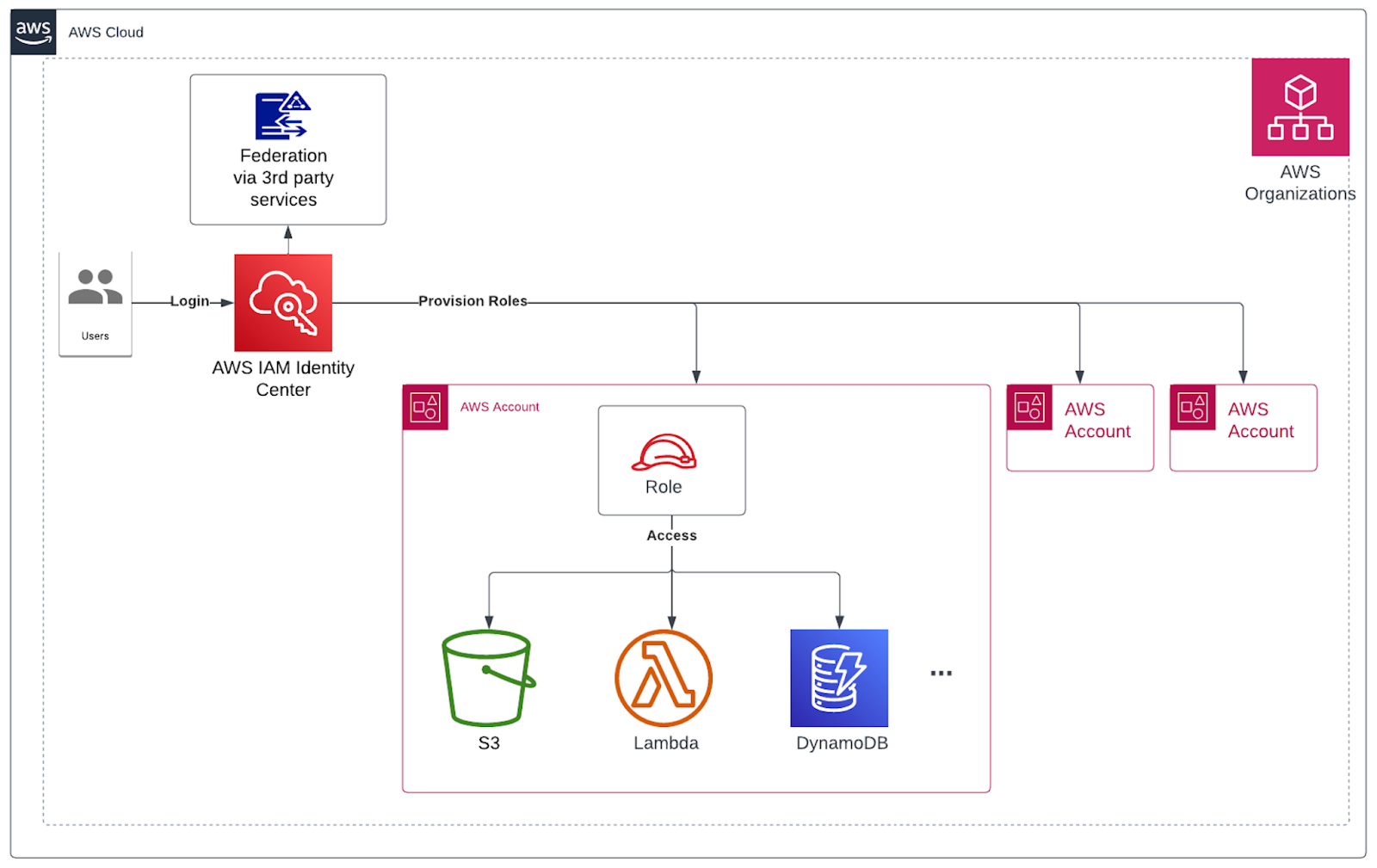
Permission Sets are resources within SSO where you can define policies for users and link them to users, groups and accounts. Under the hood, SSO creates IAM Roles to enforce these policies. By default, users and permission sets in IAM Identity Center are administered by the management account in an organisation.
AWS CloudTrail
Category: Detection and Monitoring
AWS CloudTrail continuously monitors and retains account activity to enable auditing, security monitoring, and operational troubleshooting. It records important information about user activity and API calls, including who made the request, the services used, the actions performed, parameters for the actions, and the response elements returned by the AWS service.
You can view, search, and download the most recent 90-day history of your account’s management operations at no additional cost in the CloudTrail console.
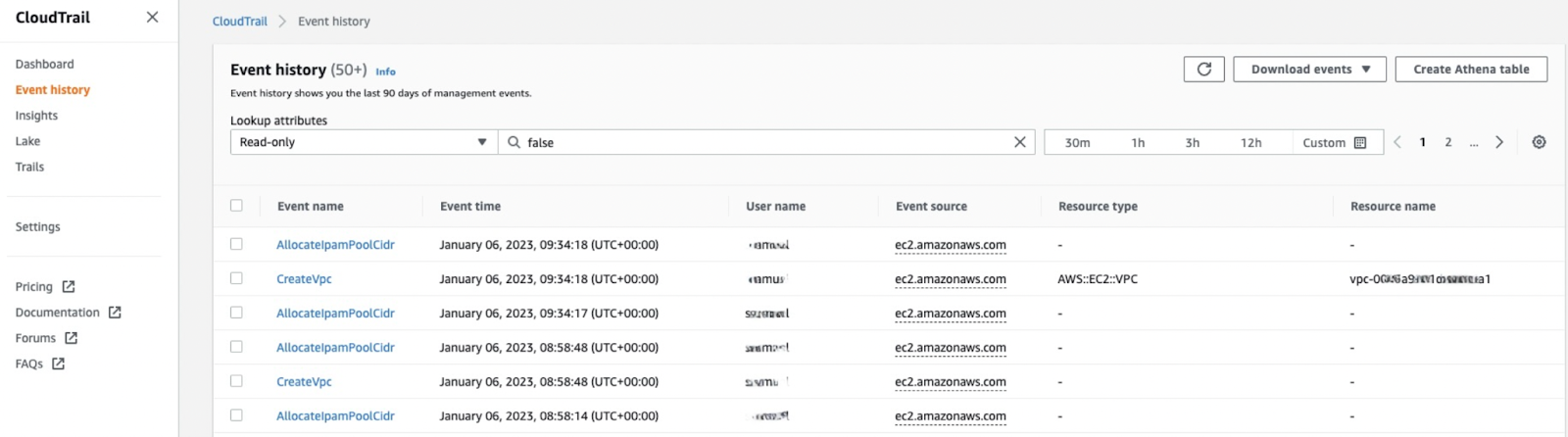
AWS CloudTrail console view
Management events provide information about management operations performed on resources such as a user signing into your account and the API calls for configuring security, logging etc. Data events are high-volume activities that provide information about the resource operations performed on or in a resource, such as:
- Lambda function execution activity
- DynamoDB object-level API activity on tables
- S3 object-level API activity etc.
By default, only management events are captured. When you create a trail, you can enable data events but there is a risk of incurring prohibitive costs if that is turned on.
If you want to archive, analyse, and respond to all events you can set up a CloudTrail trail to deliver your CloudTrail events to S3, CloudWatch Logs, and EventBridge. With multiple trails, different stakeholders, such as security administrators, software developers, and IT auditors can create and manage their own trails.
AWS IAM Access Analyzer
Category: Identity and Access Management
IAM Access Analyzer analyses your CloudTrail events to identify actions and services that have been used by an IAM entity (user or role). This can be used to refine the entity’s permissions to work towards least privileged access.
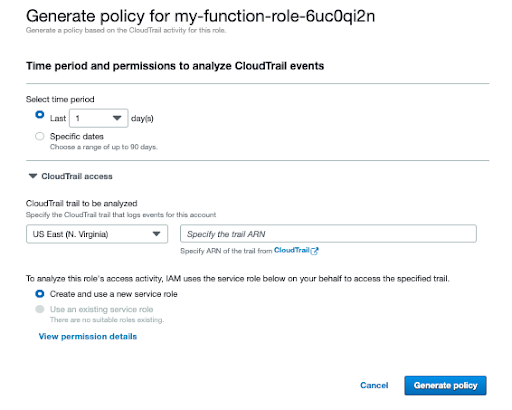
IAM – Policy generation
Since IAM Access Analyzer works based on CloudTrail logs, it doesn’t capture all IAM accesses, only captures supported, management operations. Data events are not captured. To some, this makes Access Analyzer essentially useless, since it only works with a subset of IAM actions. You can read ‘things to know about generating policies‘ in the AWS documentation to find out more.
AWS Config
Category: Detection and Monitoring
AWS Config records information about AWS resources as they are created and updated. This recorded information can be viewed and queried, but it is also used to evaluate rules to check compliance with your policies and standards. For example, if your S3 buckets need to be encrypted at all times, you can use Config to evaluate those resources and flag them as non-compliant if any of them are not currently encrypted.
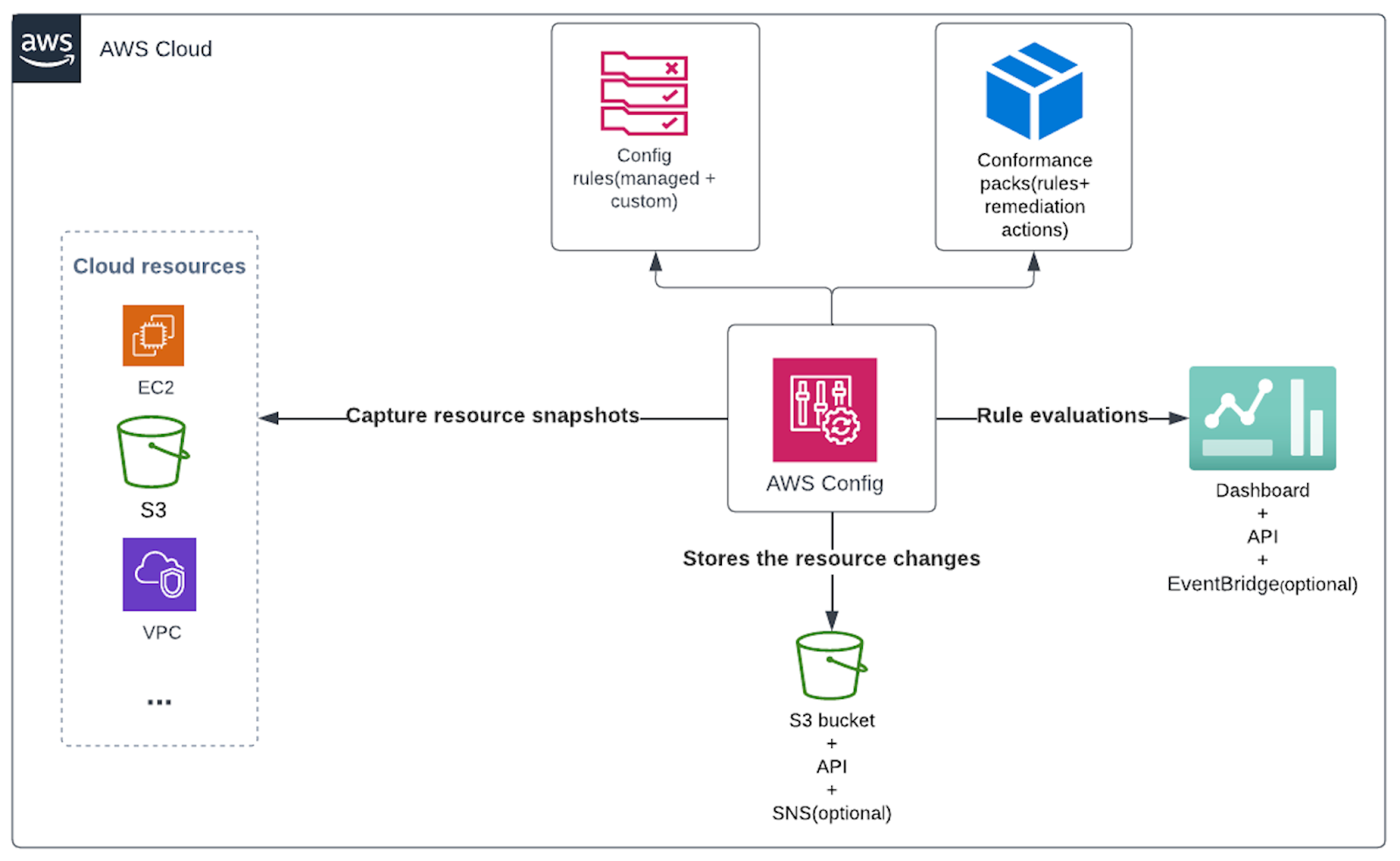
AWS Config conformance packs provide a framework to build and deploy compliance packages across several accounts/regions. This can be used to build customised packages containing AWS Config rules and remediation actions that your governance policies require. The AWS Config rules dashboard gives you an overview of resources tracked by AWS Config and a summary of current compliance by resource and by rule.
One of the limitations of AWS Config is its poor coverage over AWS services. The list of resources that AWS Config supports is here. Also, it costs money – $0.003 per configuration item recorded in your AWS account per AWS Region. It can get quite expensive when you start using AWS Config Rules – $0.001 per rule evaluation per region with some tiered discount. See AWS Config Pricing for the latest pricing information.
Amazon GuardDuty
Category: Threat Detection and Monitoring
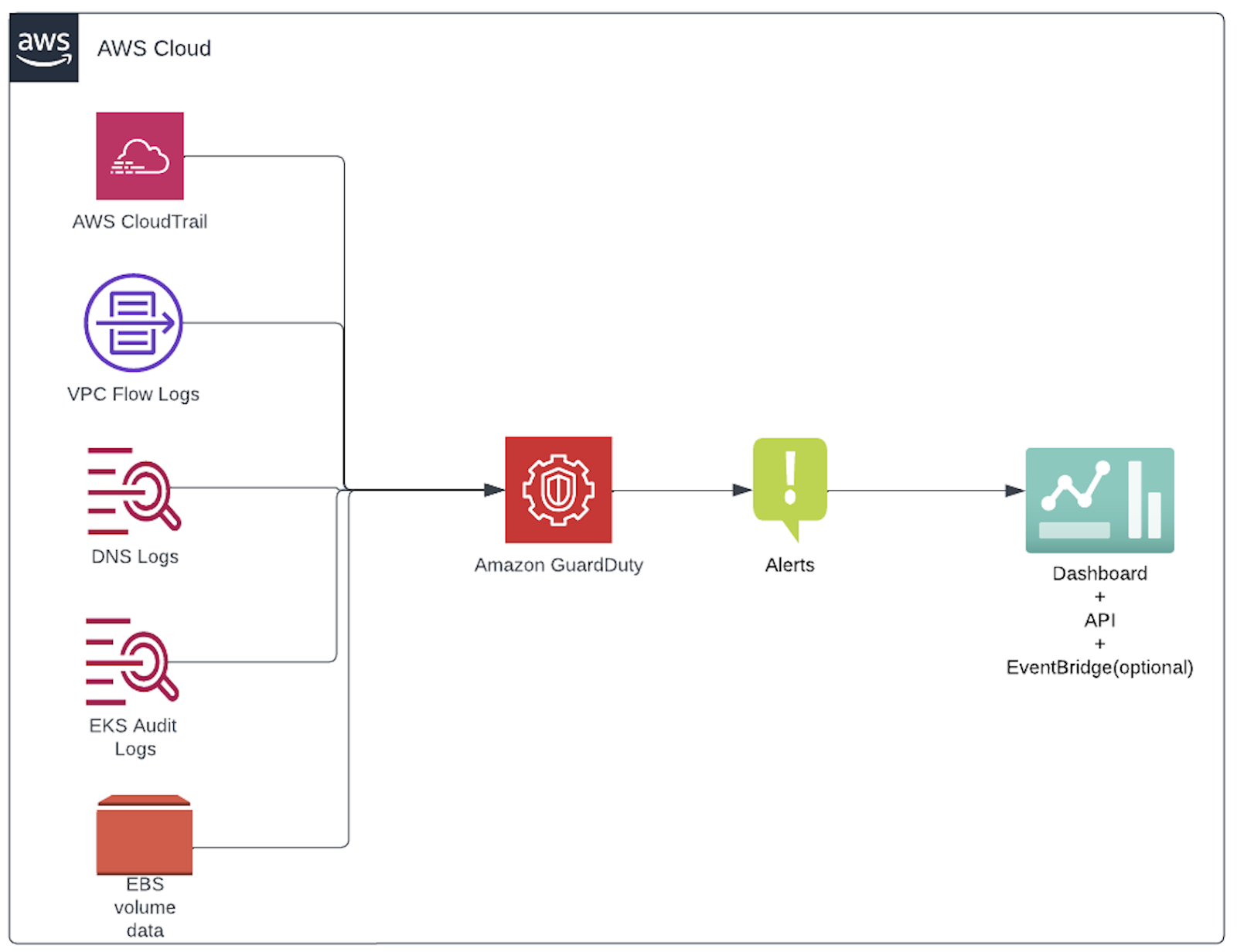
Amazon GuardDuty enables continuous monitoring of your accounts, workloads, and data stored in S3 to identify threats such as attacker reconnaissance, instance compromise, account compromise, and bucket compromise. It analyses continuous streams of account and network activity metadata from CloudTrail, VPC Flow Logs, and DNS Logs in near real-time. It then generates alerts of suspicious activity such as:
- Unusual API activity
- Unusual patterns of failed login requests
- Intra-VPC port scanning
- Instance communication with a known malicious IP
- Temporary Amazon EC2 credentials used by an external IP address
- Data exfiltration using DNS
- Unusual S3 API activity from a remote host etc.
When a threat is detected, Amazon GuardDuty delivers a detailed security finding to the GuardDuty console and EventBridge.
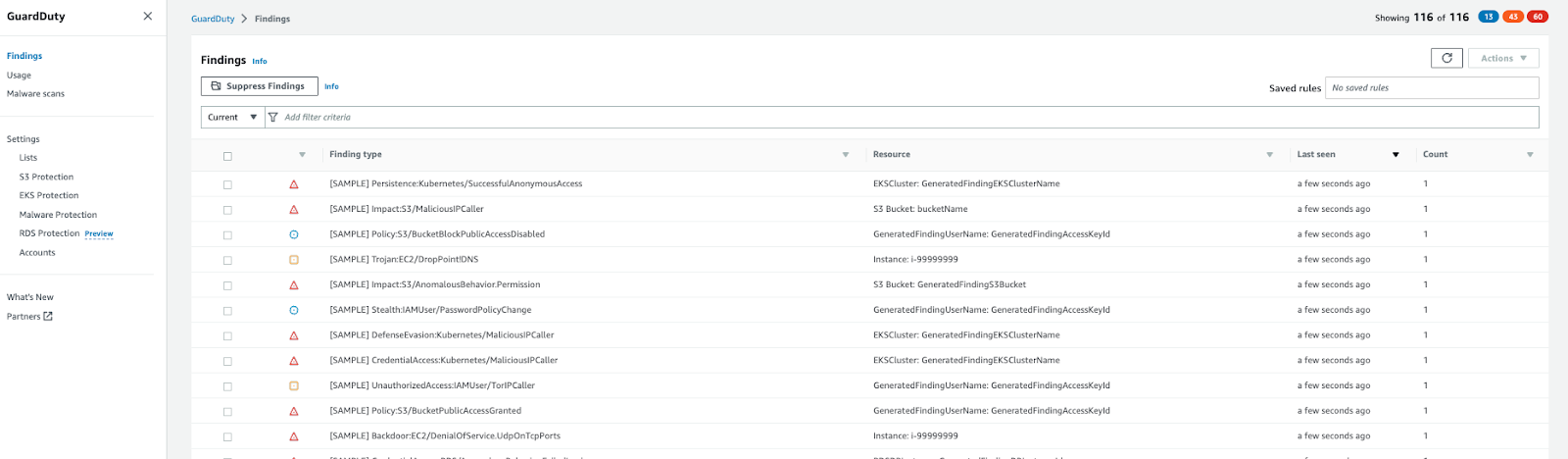
Amazon GuardDuty console view
GuardDuty pulls independent streams of data directly from Amazon CloudTrail, VPC Flow Logs, and Amazon DNS logs. So you don’t have to enable these services for it to work. All data consumed by GuardDuty is analysed and discarded. You are charged based on the volume of events analysed. You can suspend or disable GuardDuty, at any time to stop GuardDuty from processing and analysing data, events, and logs.
Amazon Inspector
Category: Detection and Monitoring
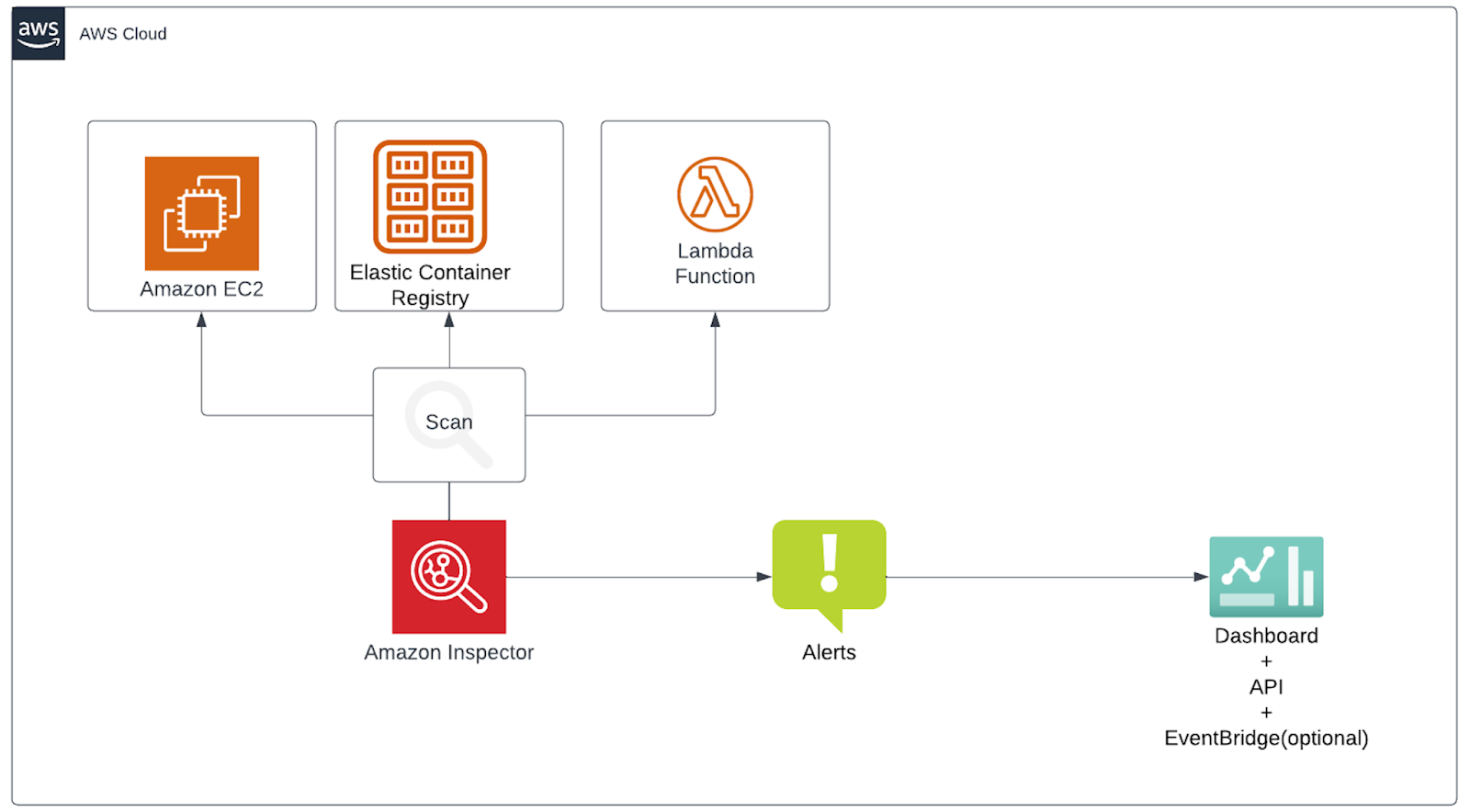
Amazon Inspector is an automated vulnerability management service that continually scans Amazon Elastic Compute Cloud (EC2), AWS Lambda functions, and container workloads for software vulnerabilities and unintended network exposure. All scanning types including; EC2 scanning, Lambda scanning, and ECR container image scanning, are activated by default. These scanning types, or indeed the service itself, can be deactivated. EC2 vulnerability scanning requires AWS Systems Manager Agent (SSM Agent). You can find resource coverage and active vulnerabilities on the dashboard.
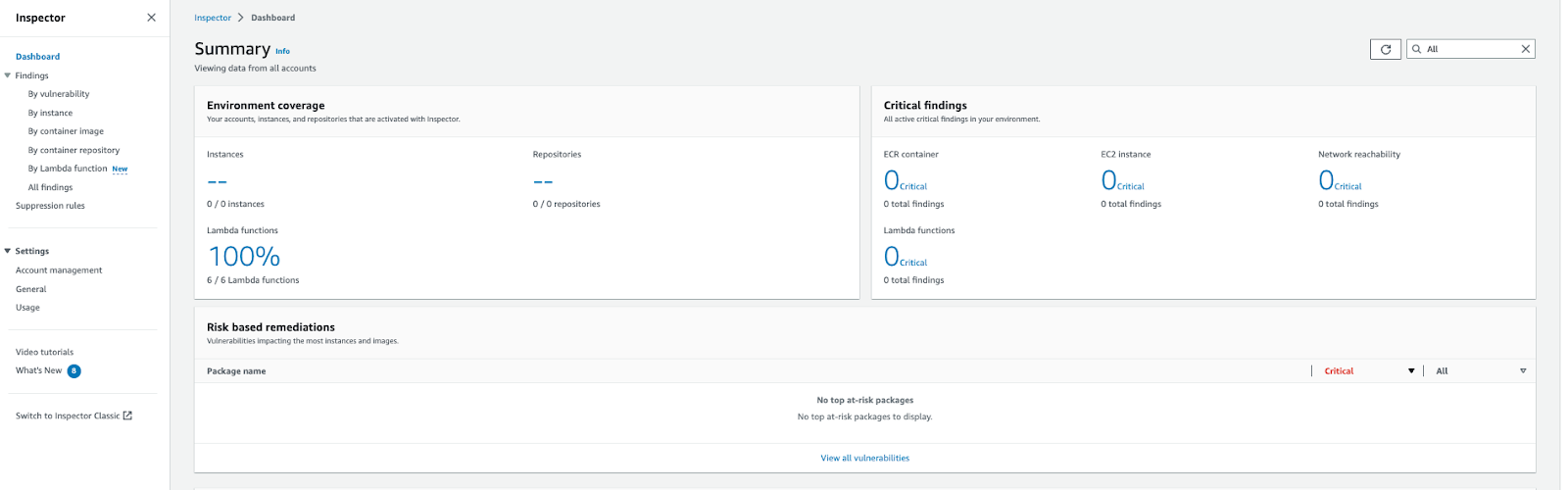
Amazon Inspector console view
Amazon Inspector scans resources that run a supported operating system or use a supported programming language. You can find the list of operating systems and languages supported here.
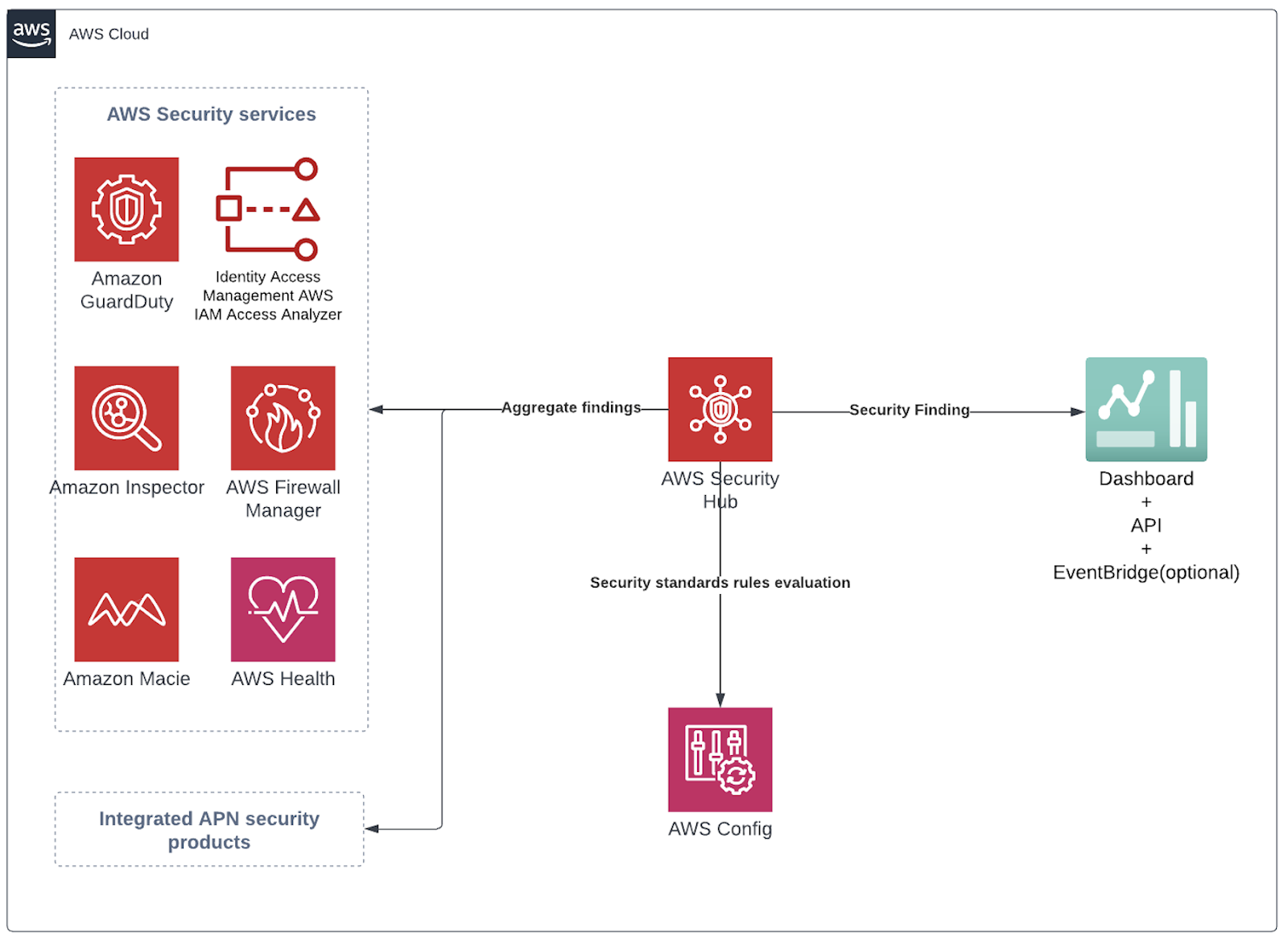
AWS Security Hub
Category: Detection and Monitoring
AWS provides many different tools for security and compliance automation. But you need to switch to each service to check the findings and compliance status. Security Hub collects findings from other AWS security services and third-party services and provides a unified view of prioritised security findings.
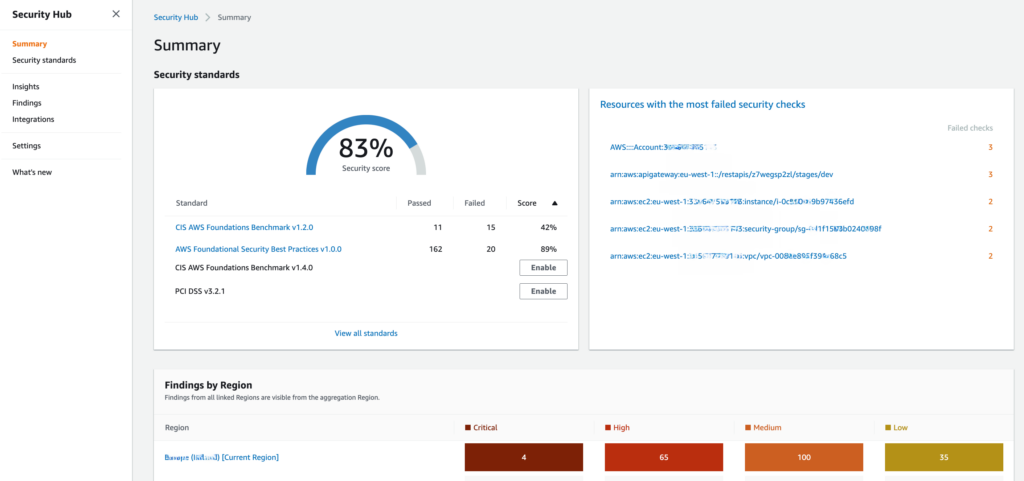
Security Hub console view
In addition, Security Hub will continuously scan your AWS accounts for configuration errors using various security standards. At the time of this writing, it supports four standards:
- AWS Foundational Security Best Practices v1.0
- CIS AWS Foundations Benchmark v1.2.0
- CIS AWS Foundations Benchmark v1.4.0
- PCI DSS v3.2.1
Security Hub enables the first two standards by default. If your organisation requires any of the supported security standard compliance checks, Security Hub will be easier to implement than deploying a customised conformance pack via AWS Config. If you want to assemble your compliance or security standard, which can include security, operational, or cost optimisation checks, AWS Config conformance packs are the way to go.
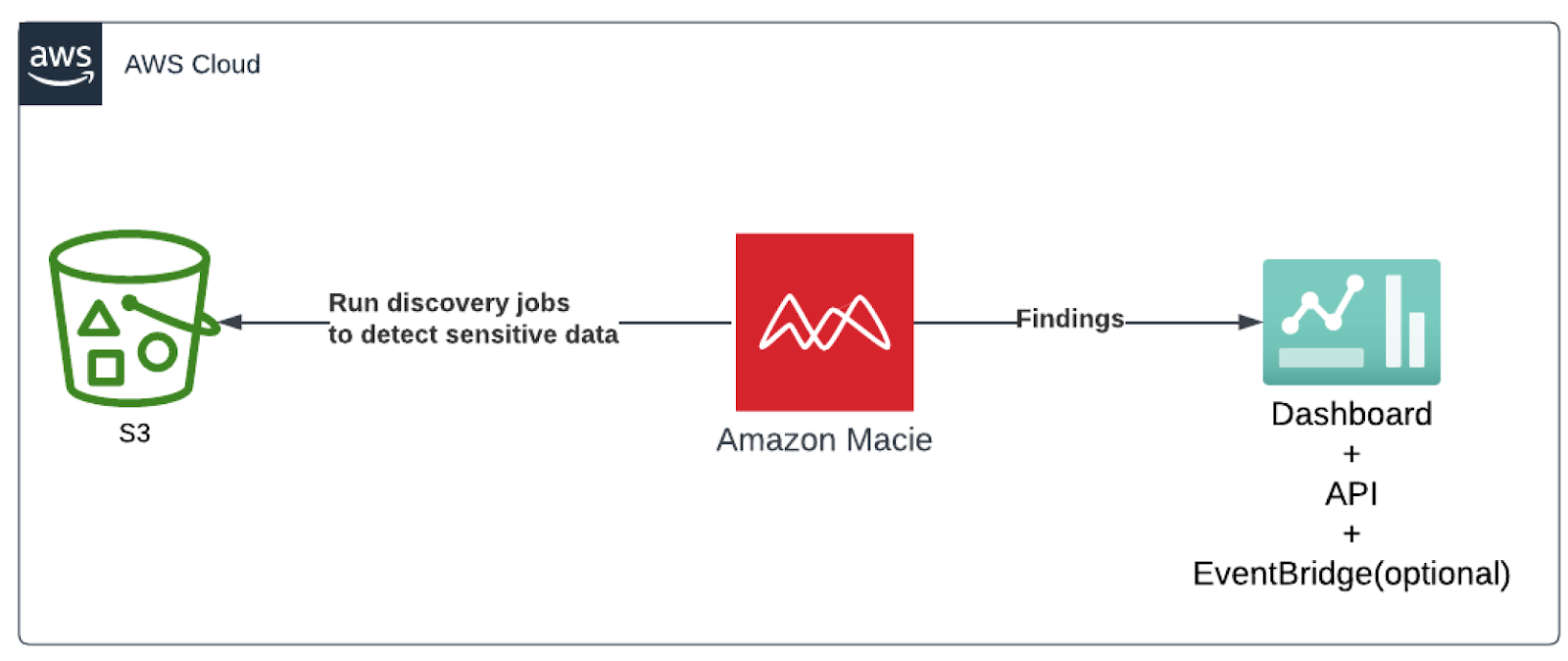
Amazon Macie
Category: Data Protection
Amazon Macie helps when organisations need to enable self-service S3 provisioning capabilities for teams and, at the same time, secure sensitive data. Macie scans all S3 buckets on a scheduled basis and detects sensitive data types including personally identifiable information (PII) such as names, addresses, credit card numbers and any custom-defined data types defined using regular expressions. If Macie detects sensitive data in an S3 object, it will generate a finding to notify you of the sensitive data. This way, Amazon Macie provides visibility into where sensitive data might reside in your Amazon S3 data estate so you can take appropriate remediation action.
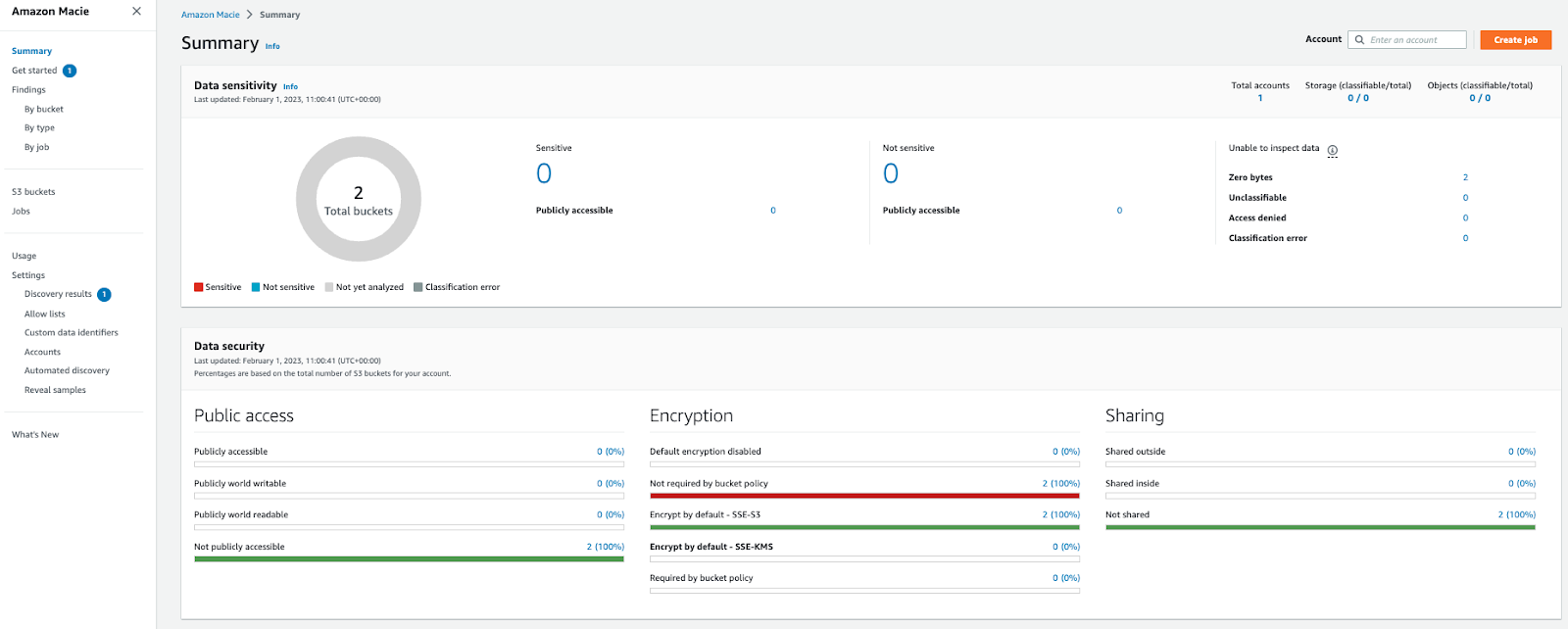
Amazon Macie console view
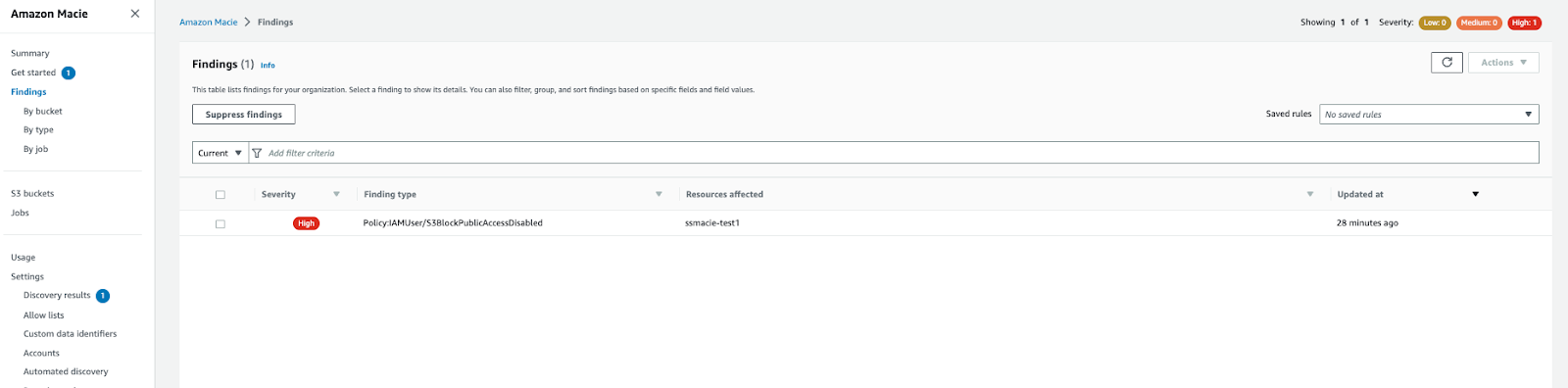
Amazon Macie console findings view
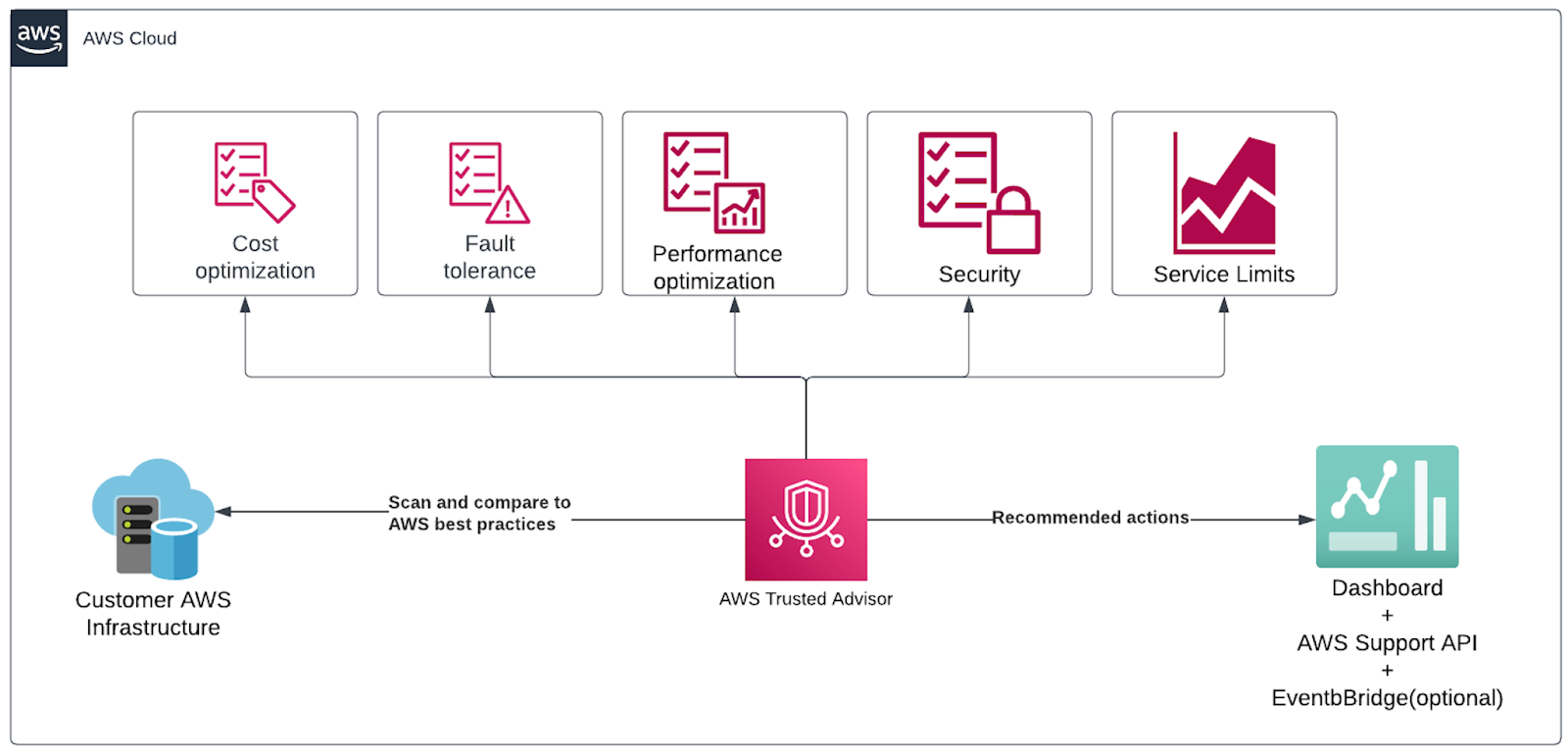
Amazon Trusted Advisor
Category: Cloud Best Practice Recommendations
Trusted Advisor is a free service that inspects your AWS environment and makes recommendations for saving money, improving system performance, or closing security gaps.
Trusted Advisor checks are not customizable, you just get the checks AWS has added. If you are looking to check compliance with security standards and best practices, use AWS Security Hub. When you have Security Hub enabled, you can view the SecurityHub findings on Trusted Advisor with Security Hub integration.
Users with Business-or Enterprise-level Support have access to all checks on console and also programmatically via the AWS Support API. Basic or Developer Support plan users get limited checks on console only.
Conclusion
AWS Security Services help organisations secure their AWS infrastructure – but it can be challenging to choose the right tools for your cloud environment. If you’re looking for solutions to specific security use cases, reach out to fourTheorem for help implementing these services as part of our AWS Foundations Accelerator.
